Threat Hunting - Simplifying The Beacon Analysis Process - Active
In part one of this two-part series, I described what is involved with performing a beacon analysis and why it is so important […]
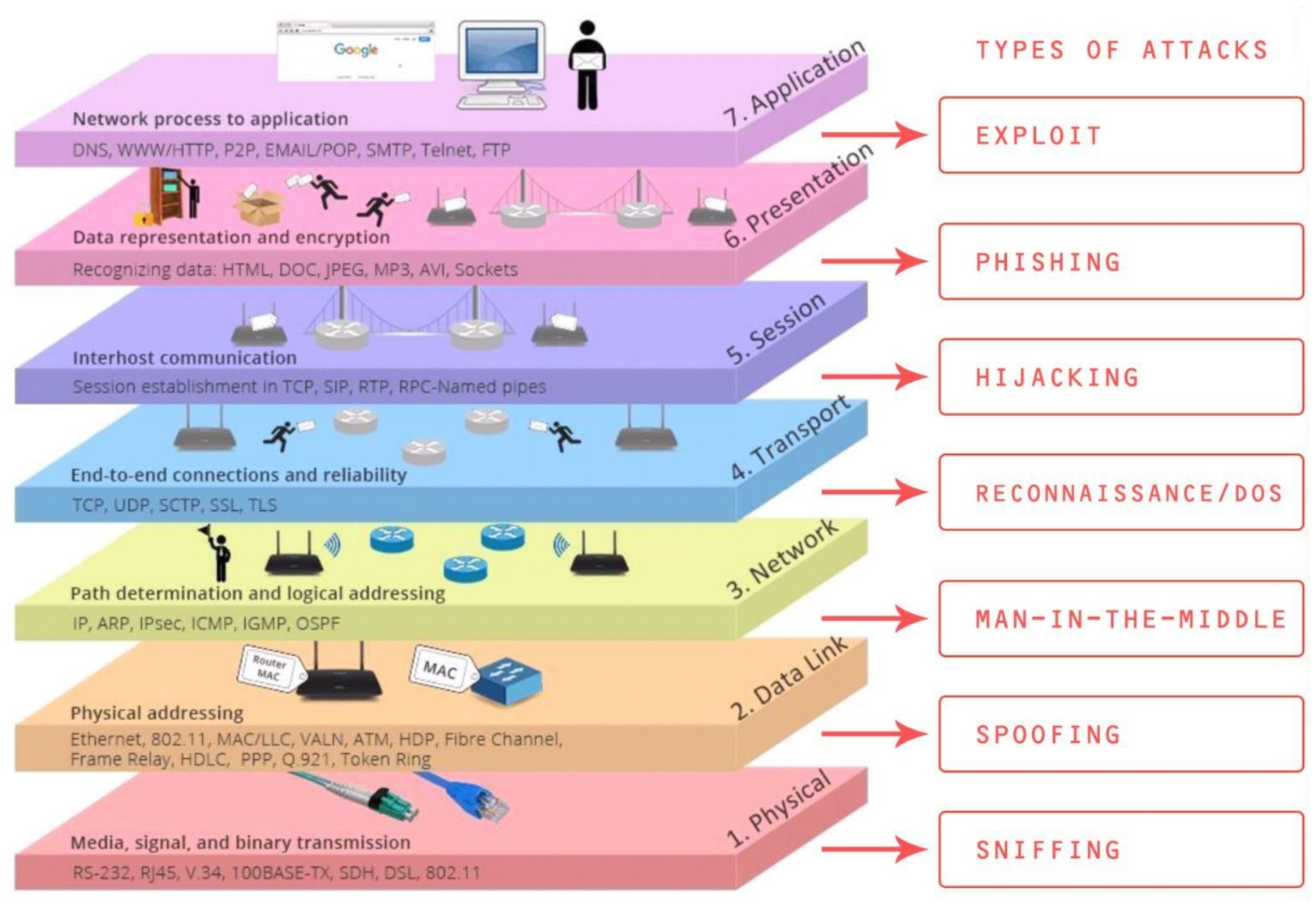
Symmetry, Free Full-Text

The Automotive Threat Modeling Template, NCC Group Research Blog

How Event ID 4702 boosts cybersecurity, Hassnain J. posted on the topic
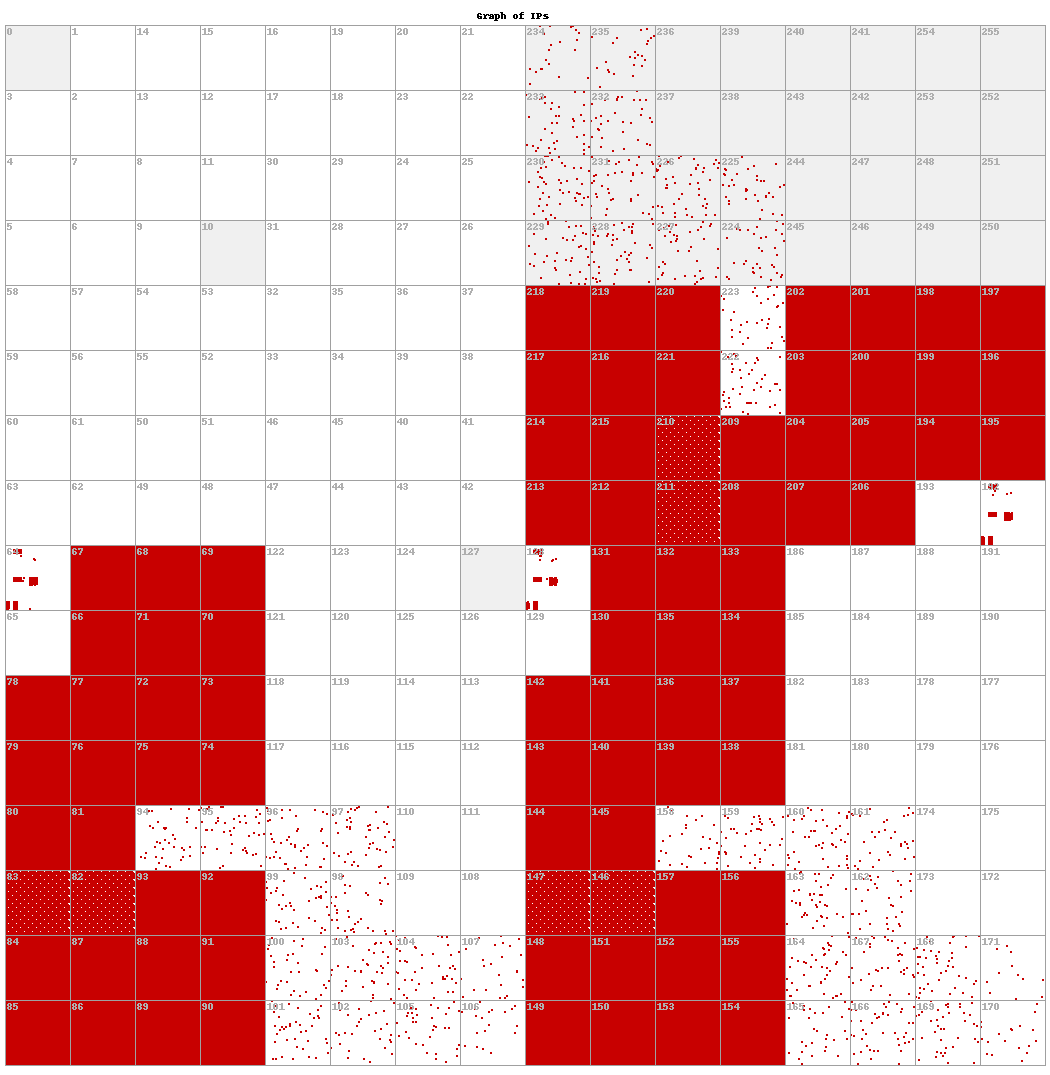
Analyzing DNS Traffic for Anomalous Domains and Threat Detection
.png?width=2000&height=800&name=Hunt%20information%20informs%20rule%20variables%20and%20level%20of%20specificity%20(1).png)
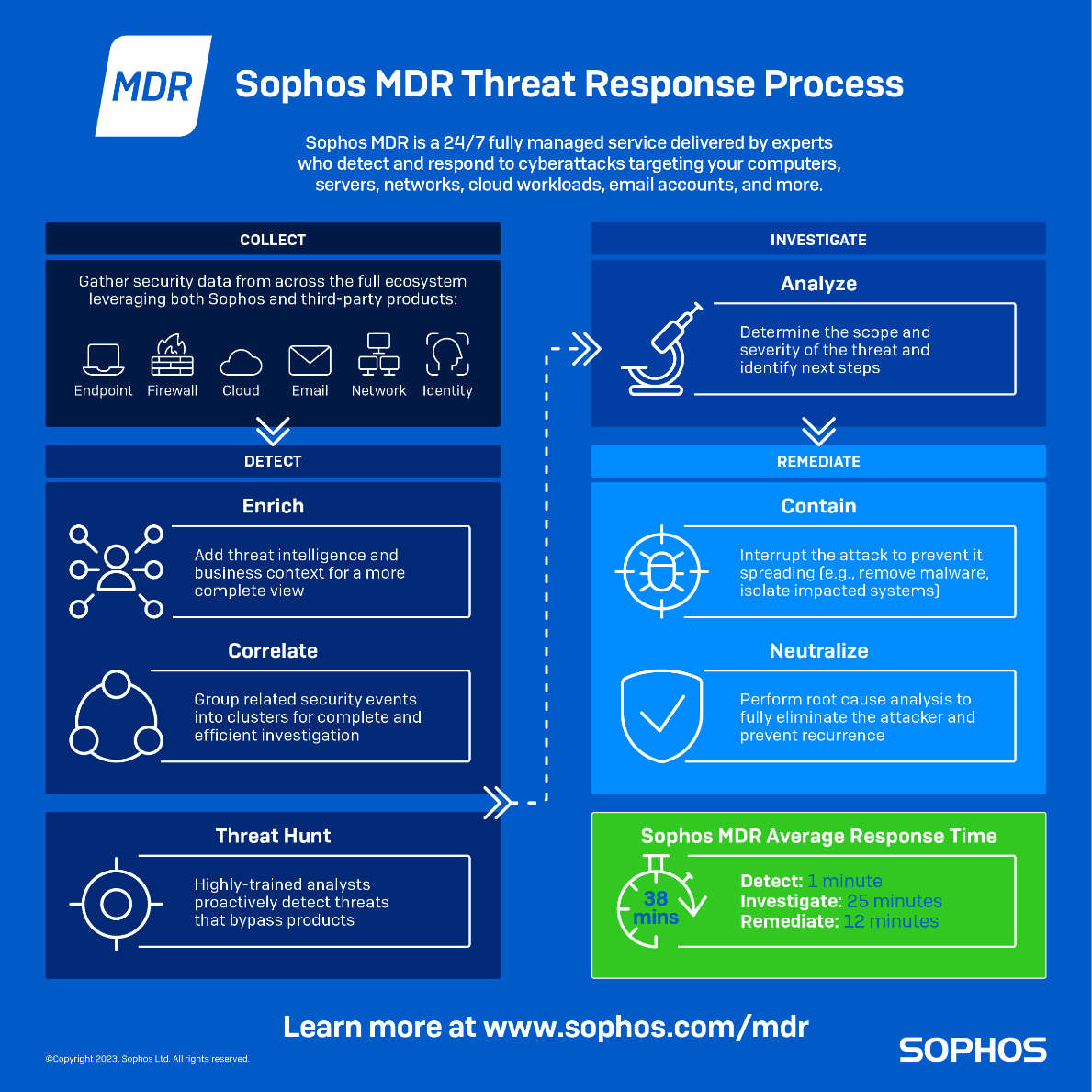
Building a better detection ecosystem

Identifying an Existing APT Intrusion - Secplicity - Security Simplified
What is Threat Hunting? Threat Hunting Explained
Webcasts - Active Countermeasures
Threat Hunting Loop (Extracted from [19])
Threat Hunting - Simplifying The Beacon Analysis Process - Active Countermeasures
Identifying beaconing malware using Elastic — Elastic Security Labs

What is Threat Hunting and Why Do All Businesses Need It?

Worm-like propagation of Sysrv-hello crypto-jacking botnet: Network traffic analysis and latest TTPs




