Four types of fake key attacks. Each diagram represents Alice (left)
Alice Whispers To Bob: At the core of privacy in the 21st Century is Extended Triple Diffie-Hellman and Ratchets, by Prof Bill Buchanan OBE, ASecuritySite: When Bob Met Alice

Kent SEAMONS Brigham Young University - Provo Main Campus, Utah

Modern Cryptanalysis Methods, Advanced Network Attacks and Cloud Security

The Plague
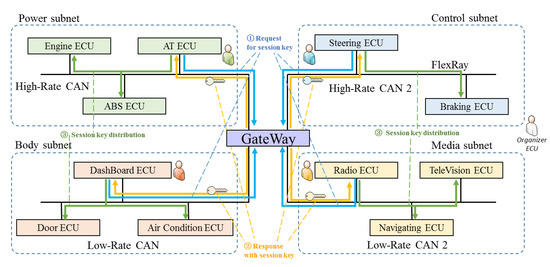
Mathematics, Free Full-Text
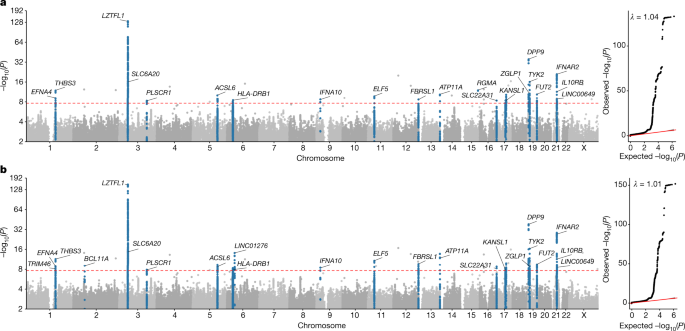
Whole-genome sequencing reveals host factors underlying critical COVID-19
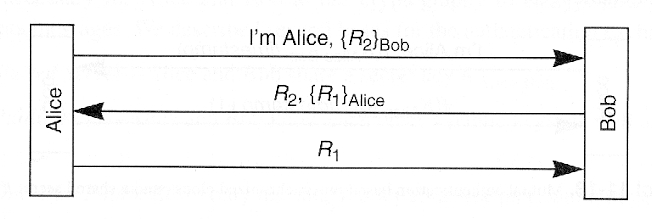
Chapter 11

Diffie–Hellman key exchange - Wikipedia

What Science Tells Us About the Effects of Gun Policies

PDF) Automatic Detection of Fake Key Attacks in Secure Messaging
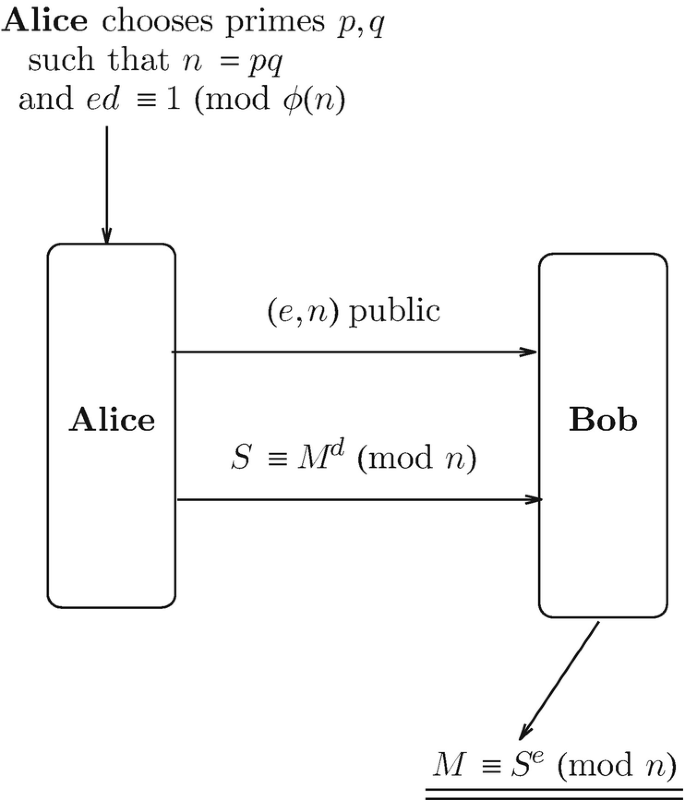
Factoring Based Cryptography

Kent SEAMONS Brigham Young University - Provo Main Campus, Utah
Suppose Alice and Bob generate 3 keys and use triple encryption. They encrypt the message using 1st key, then encrypt the result using 2nd key, then encrypt the result again using 3rd

Amir HERZBERG, Professor, Professor









