Four types of fake key attacks. Each diagram represents Alice
Download scientific diagram | Four types of fake key attacks. Each diagram represents Alice (left), her contacts (right), and an adversary (center). The green lines represent secure connections; the red lines represent compromised connections. Note that in each situation, there may be other pairs of clients communicating securely that are not shown. from publication: Automatic Detection of Fake Key Attacks in Secure Messaging | Popular instant messaging applications such as WhatsApp and Signal provide end-to-end encryption for billions of users. They rely on a centralized, application-specific server to distribute public keys and relay encrypted messages between the users. Therefore, they prevent | Automatism, Security and Server | ResearchGate, the professional network for scientists.
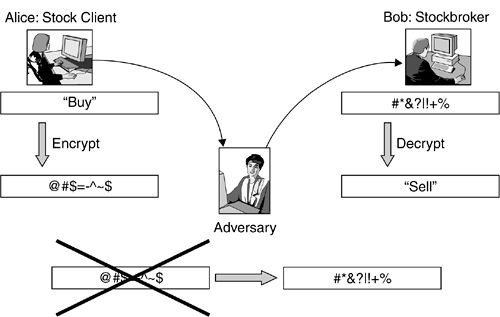
Public-Key Cryptography, The Theory of Cryptography

Meet The First Couple of Cryptography – Alice and Bob

Phases of ethical hacking. Download Scientific Diagram

Four types of fake key attacks. Each diagram represents Alice (left)
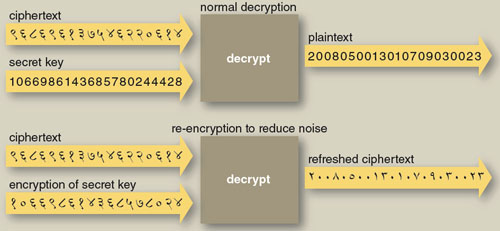
Alice and Bob in Cipherspace

Amir HERZBERG, Professor, Professor
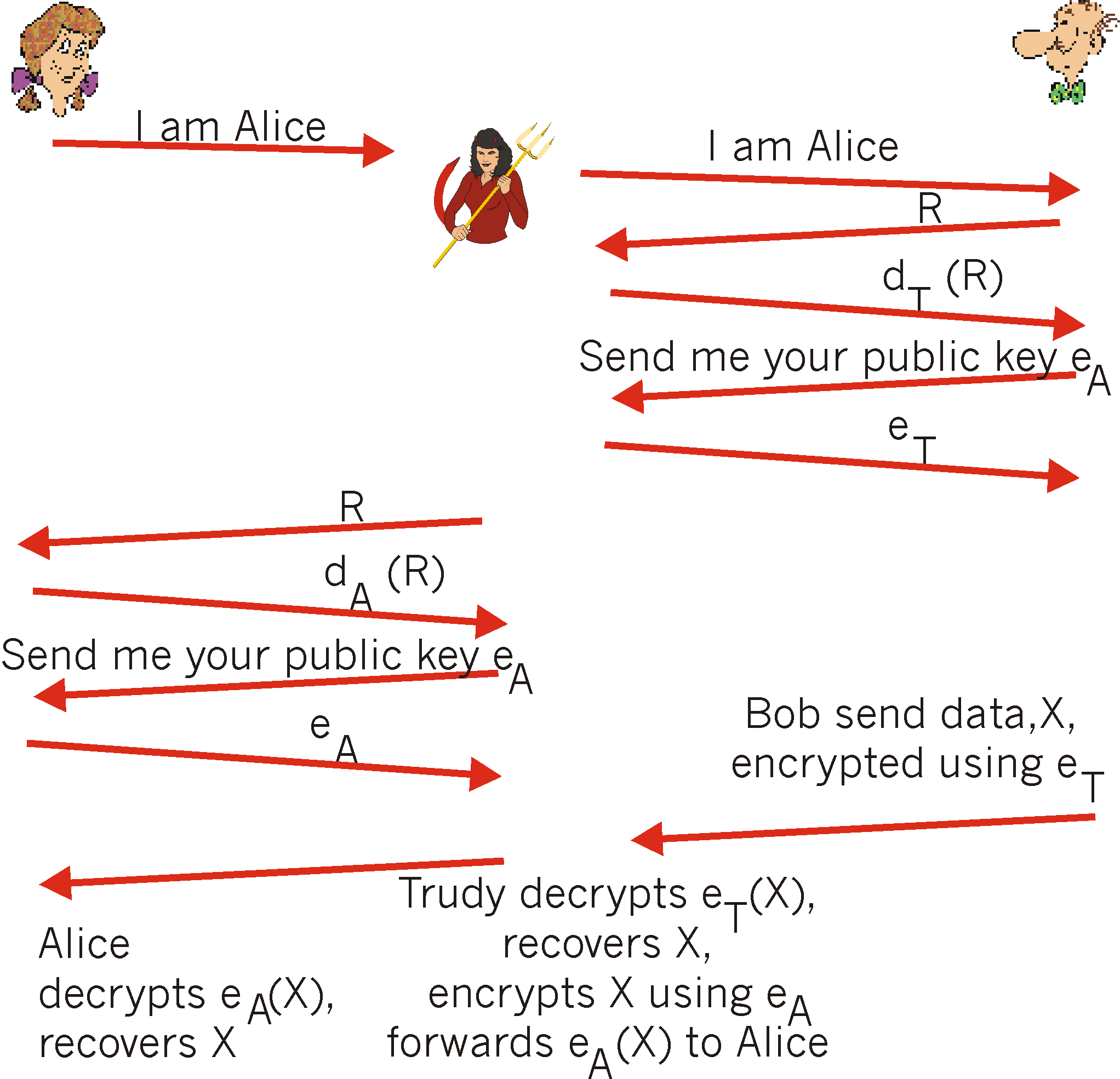
Authentication

Applied Sciences, Free Full-Text

Devashish GOSAIN, Postdoc, PhD









